Introduction to Computer System
A computer is an intricate electronic device that operates based on programmed instructions to receive input data, process it, and produce output results. When combined with additional hardware and software, it forms a comprehensive system known as a computer system.
The fundamental components of a computer system include the central processing unit (CPU), which acts as the brain of the system, memory for temporary data storage, input/output devices for interacting with the user and other systems, and storage devices for long-term data retention. These components work collaboratively as a cohesive unit to generate the desired outcomes.
Computer systems are available in various forms and sizes, ranging from powerful servers used in large-scale operations to personal devices like desktop computers, laptops, tablets, and smartphones designed for individual use. The versatility and scalability of computer systems allow them to adapt to diverse needs and environments.
The block diagram depicted in Figure 1 illustrates the interconnected components of a computer system, showcasing the flow of data and signals between these elements to facilitate seamless operation and data processing.
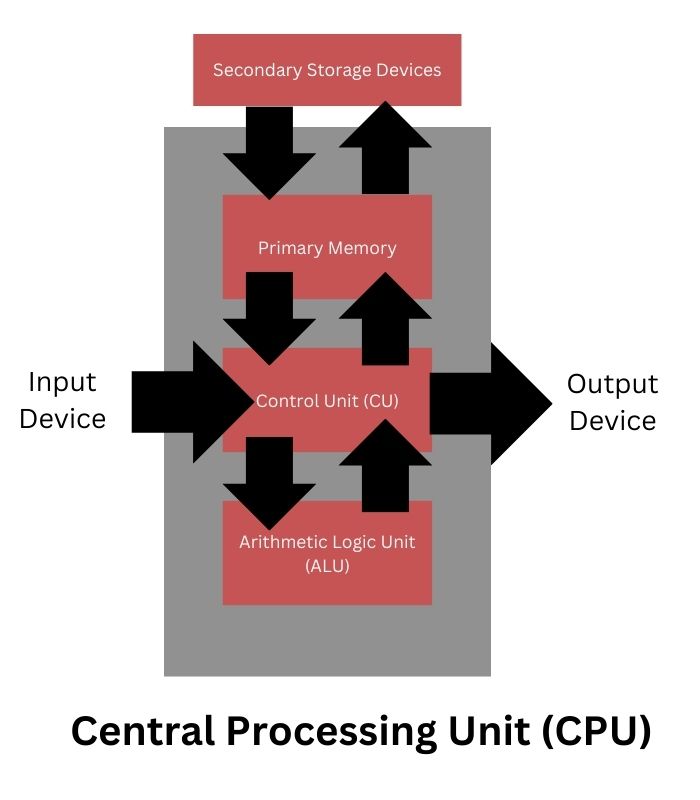
Central Processing Unit (CPU)
The Central Processing Unit (CPU), often referred to as the brain of a computer, is the electronic circuitry responsible for carrying out actual processing tasks. It can be thought of as the command center that executes instructions and manipulates data within a computer system. Physically, a CPU can consist of one or multiple microchips known as integrated circuits (IC), which are composed of semiconductor materials.
The functioning of a CPU revolves around receiving instructions and data through programs. These instructions are fetched from memory, and the CPU then executes arithmetic and logic operations based on these instructions, storing the results back into memory. During this process, the CPU utilizes its local memory known as registers. Registers are limited in size and number but are crucial for temporarily storing data, instructions, or intermediate results during processing.
The CPU comprises two primary components: the Arithmetic Logic Unit (ALU) and the Control Unit (CU). The ALU handles arithmetic operations like addition, subtraction, multiplication, and division, as well as logic operations such as AND, OR, and NOT, as dictated by the instructions in a program. On the other hand, the CU is responsible for coordinating the execution of instructions in sequence, interpreting these instructions, and managing the flow of data between the CPU, memory, and input/output devices.
In addition to its core components, the CPU is also commonly known as a microprocessor, emphasizing its role as a miniature yet powerful processing unit within a computer system.
Input Devices
Input devices are crucial components of a computer system responsible for sending control signals to the computer. These devices play a vital role in converting input data into a digital format that can be processed by the computer. Examples of input devices include keyboards, mice, scanners, touchscreens, and more. Additionally, specialized braille keyboards are available to assist visually impaired individuals in entering data into computers.
Advancements in technology have also introduced voice input as a method of data entry. For instance, platforms like Google Voice Search allow users to input search queries using their voice instead of typing. This functionality has greatly enhanced accessibility and convenience in interacting with computer systems.

When data is entered through an input device, it is temporarily stored in the computer’s main memory, also known as RAM (Random Access Memory). However, for permanent storage and future retrieval, both data and instructions are stored in additional storage locations known as secondary memory devices, such as hard drives, solid-state drives, or external storage devices. This separation of temporary and permanent storage ensures that data can be accessed efficiently during processing and preserved for long-term use.
Output Devices
An output device in a computer system receives data from the computer and converts it into a format that humans can understand. These devices are essential for displaying information, producing physical copies, and facilitating communication with users. Common examples of output devices include monitors, projectors, headphones, speakers, and printers, each serving unique purposes.
For individuals with visual impairments, specialized output devices like braille display monitors are invaluable. These devices translate digital information into braille, enabling visually challenged individuals to comprehend textual output generated by computers.
Among output devices, printers play a significant role in obtaining physical copies (hardcopies) of digital content. There are three main types of printers widely used today: inkjet printers, laserjet printers, and dot matrix printers. Additionally, the advent of 3D printing technology has revolutionized manufacturing and medical fields. 3D printers can construct physical replicas of digital 3D designs, making them indispensable for creating prototypes in manufacturing industries and exploring possibilities like organ printing in the medical sector.
Evolution of Computer
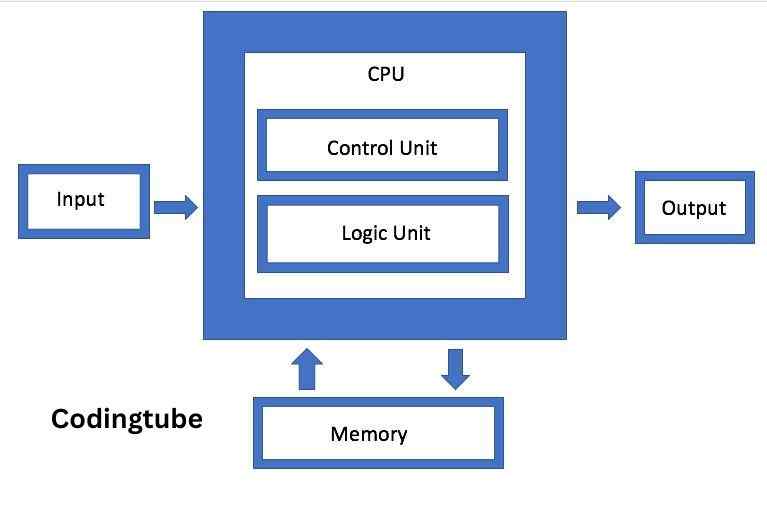
The evolution of computing devices spans from simple calculators to modern-day powerful data processors, showcasing significant advancements in a relatively short timeframe. The Von Neumann architecture, depicted in Figure 2, serves as a foundational model comprising a Central Processing Unit (CPU) for executing arithmetic and logical instructions, memory for data and program storage, input/output devices, and communication channels for data exchange.
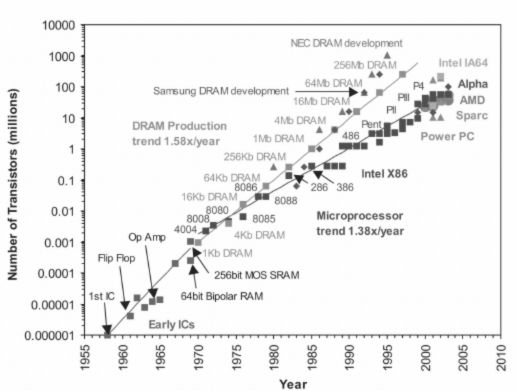
The Electronic Numerical Integrator and Computer (ENIAC) marked a pivotal moment as the first binary programmable computer based on Von Neumann architecture. As technology progressed, the 1970s witnessed Large Scale Integration (LSI), enabling the integration of an entire CPU onto a single chip known as a microprocessor. Moore’s Law accurately predicted the exponential increase in transistor density on microchips, driving advancements like Very Large Scale Integration (VLSI) in the 1980s, packing around 3 million components on a small-sized chip.
The concept of Super Large Scale Integration (SLSI) emerged, showcasing the capability to incorporate approximately 106 components on a single Integrated Circuit (IC), as shown in Figure 1.6. This rapid progression led to milestones like IBM’s introduction of the first personal computer (PC) for home use in 1981 and Apple’s Macintosh machines in 1984. The adoption of Graphical User Interface (GUI) operating systems by Microsoft and others further popularized PCs over command-line interface systems like UNIX or DOS.
The 1990s witnessed the explosive growth of the World Wide Web (WWW), fueling widespread computer usage and cementing computers as integral to daily life. Subsequent innovations brought about portable computing through laptops, followed by smartphones, tablets, and other personal digital assistants, leveraging advancements in processor miniaturization, faster memory, and high-speed connectivity.
The current wave of computing includes wearable gadgets such as smartwatches, smart lenses, headbands, and headphones, alongside smart appliances integrating into the Internet of Things (IoT) ecosystem. These devices harness the power of Artificial Intelligence (AI), marking the continual evolution and integration of computing technology into various aspects of modern life.
Computer Memory
In the realm of computing, memory plays a pivotal role as a fundamental component that facilitates data storage, retrieval, and processing. Computer memory can be broadly categorized into primary memory (main memory) and secondary memory (storage devices), each serving distinct functions and purposes within a computer system. In this comprehensive guide, we delve into the intricacies of computer memory, exploring its types, functions, and significance in modern computing.
1. Primary Memory (Main Memory):
Primary memory, also known as main memory or internal memory, refers to the immediate storage space directly accessible by the Central Processing Unit (CPU) during program execution. This type of memory is volatile, meaning it loses its contents when the power supply is turned off. Primary memory is crucial for storing active programs, data, and instructions required for real-time processing. Key components of primary memory include:
a. Random Access Memory (RAM):
RAM is the primary workspace for a computer system, providing fast access to data and instructions during processing. It acts as a temporary storage medium, holding currently running programs, application data, and intermediate results. RAM’s volatile nature allows for quick read and write operations, making it essential for multitasking and efficient program execution.
b. Read-Only Memory (ROM):
ROM is a non-volatile memory type that retains its contents even when power is removed. It stores essential firmware, boot loaders, and system-level programs needed for the computer to start up and initialize hardware components. Unlike RAM, ROM is typically used for storing permanent instructions that do not change frequently, ensuring system stability and functionality.
2. Secondary Memory (Storage Devices):
While primary memory caters to immediate processing needs, secondary memory serves as a long-term storage solution for preserving data, instructions, and programs beyond volatile memory limitations. Secondary memory devices have larger storage capacities but are comparatively slower in access speeds. Common examples of secondary memory devices include:
a. Hard Disk Drives (HDDs):
HDDs utilize rotating magnetic disks to store and retrieve data. They offer high storage capacities at relatively low costs, making them ideal for storing large volumes of files, applications, and operating systems. However, HDDs have slower read/write speeds compared to solid-state drives (SSDs).
b. Solid State Drives (SSDs):
SSDs employ flash memory technology to store data, resulting in significantly faster read/write speeds than HDDs. They are more energy-efficient, durable, and resistant to physical shock. SSDs are commonly used in modern computing devices, providing rapid access to data and improving overall system performance.
c. Optical Storage Devices (CDs, DVDs, Blu-ray Discs):
Optical storage devices use laser technology to read and write data on optical discs such as CDs, DVDs, and Blu-ray discs. They offer removable, portable storage solutions for media files, software installations, and backups.
d. Flash Drives (USB Drives):
Flash drives, also known as USB drives or thumb drives, are compact and portable secondary storage devices. They use flash memory technology to store data and can be easily connected to computers for data transfer, file storage, and backup purposes.

Importance of Computer Memory:
Computer memory is essential for seamless and efficient operation of computing systems. Here are key points highlighting the importance of memory in modern computing:
- Fast Data Access: Primary memory like RAM enables quick access to data and instructions, enhancing overall system performance and responsiveness.
- Multitasking Capabilities: Ample memory allows for running multiple programs simultaneously without significant performance degradation.
- Data Persistence: Secondary memory ensures data persistence by providing long-term storage solutions for files, documents, programs, and system configurations.
- System Stability: ROM and primary memory contribute to system stability by storing essential firmware, boot loaders, and critical system instructions.
- Optimized Workflows: Efficient memory management leads to optimized workflows, faster processing times, and improved user experiences.
- Scalability: Expandable memory options allow for scalability, accommodating increasing data storage and processing demands over time.
Data Transfer between Memory and CPU
Data need to be transferred between the CPU and primary memory as well as between the primary and secondary memory. Data are transferred between different components of a computer system using physical wires called bus. For example, bus is used for data transfer between a USB port and hard disk or between a hard disk and main memory. Bus is of three types— (i) Data bus to transfer data between different components, (ii) Address bus to transfer addresses between CPU and main memory. The address of the memory location that the CPU wants to read or write from is specified in the address bus, and (iii) Control bus to communicate control signals between different components of a computer.
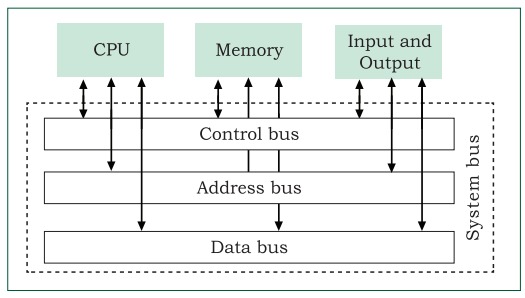
All these three buses collectively make the system bus, as shown in Figure 1.8. As the CPU interacts directly with main memory, any data entered from input device or the data to be accessed from hard disk needs to be placed in the main memory for further processing. The data is then transferred between CPU and main memory using bus. The CPU places on the address bus, the address of the main memory location from which it wants to read data or to write data. While executing the instructions, the CPU specifies the read or write control signal through the control bus. As the CPU may require to read data from main memory or write data to main memory, a data bus is bidirectional. But the control bus and address bus are unidirectional. To write data into memory, the CPU places the data on the data bus, which is then written to the specific address provided through the address bus. In case of read operation, the CPU specifies the address, and the data is placed on the data bus by a dedicated hardware, called memory controller. The memory controller manages the flow of data into and out of the computer’s main memory.
Microprocessors
In earlier days, a computer’s CPU used to occupy a large room or multiple cabinets. However, with advancement in technology, the physical size of CPU has reduced and it is now possible to place a CPU on a single microchip only. A processor (CPU) which is implemented on a single microchip is called microprocessor. Nowadays, almost all the CPUs are microprocessors. Hence, the terms are used synonymously for practical purpose.
Microprocessor is a small-sized electronic component inside a computer that carries out various tasks involved in data processing as well as arithmetic and logical operations. These days, a microprocessor is built over an integrated circuit comprising millions of small components like resistors, transistors and diodes.
Microprocessors have evolved over time in terms of their increased processing capability, decreasing physical size and reduced cost. Currently available microprocessors are capable of processing millions of instructions per millisecond. Table 1 lists different types of microprocessors along with their generation, time period, and underlying technology since their inception in early 1970s.
| Generation | Time Period | Key Features |
|---|---|---|
| 1st Generation | 1971-1972 | Intel 4004 – 4-bit microprocessor |
| Limited performance, used in calculators | ||
| 2nd Generation | 1973-1978 | Intel 8008, 8080, Motorola 6800 |
| 8-bit architecture, improved performance | ||
| 3rd Generation | Late 1970s-1985 | Intel 8085, 8086, Zilog Z80, Motorola 68000 |
| 16-bit architecture, introduction of microcomputers | ||
| 4th Generation | 1985-1995 | Intel 80386, 80486, Motorola 68030 |
| 32-bit architecture, improved performance | ||
| 5th Generation | 1995-2000 | Intel Pentium series, AMD K5/K6 |
| Introduction of superscalar architecture | ||
| 6th Generation | 2000-2006 | Intel Pentium 4, AMD Athlon XP |
| Higher clock speeds, improved multimedia support | ||
| 7th Generation | 2006-2012 | Intel Core 2 series, AMD Phenom |
| Dual-core and quad-core processors | ||
| 8th Generation | 2012-2019 | Intel Core i series, AMD Ryzen |
| Multicore processors, integrated graphics | ||
| 9th Generation | 2019-present | Intel Core i9, AMD Ryzen 9 |
| High-performance computing, AI integration |
Microprocessor Specifications
Microprocessors are classified on the basis of different features which include chip type, word size, memory size, clock speed, etc. These features are briefly explained below:
Word Size
Word size is the maximum number of bits that a microprocessor can process at a time. Earlier, a word was of 8 bits, as it was the maximum limit at that time. At present, the minimum word size is 16 bits and maximum word size is 64 bits
Memory Size
Depending upon the word size, the size of RAM varies. Initially, RAM was very small (4MB) due to 4/8 bits word size. As word size increased to 64 bits, it has become feasible to use RAM of size upto 16 Exabytes (EB).
Clock Speed
Computers have an internal clock that generates pulses (signals) at regular intervals of time. Clock speed simply means the number of pulses generated per second by the clock inside a computer. The clock speed indicates the speed at which the computer can execute instructions. Earlier, it was measured in Hertz (Hz) and Kilohertz (kHz). But with advancement in technology and chip density, it is now measured in Gigahertz (GHz), i.e., billions of pulses per second.
Cores
Core is a basic computation unit of the CPU. Earlier processors had only one computation unit, thereby capable of performing only one task at a time. With the advent of multicore processor, it has become possible for the computer to execute multiple tasks, thereby increasing the system’s performance. CPU with two, four, and eight cores is called dual-core, quad-core and octa-core processor, respectively.
Microcontrollers
The microcontroller is a small computing device which has a CPU, a fixed amount of RAM, ROM and other peripherals all embedded on a single chip as compared to microprocessor that has only a CPU on the chip. The structure of a microcontroller is shown in Figure 1.9. Keyboard, mouse, washing machine, digital camera, pendrive, remote controller, microwave are few examples of microcontrollers. As these are designed for specific tasks only, hence their size as well as cost is reduced.
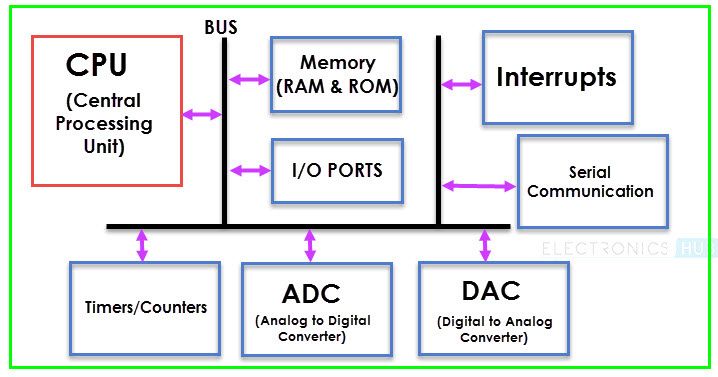
Because of the very small size of the microcontroller, it is embedded in another device or system to perform a specific functionality. For example, the microcontroller in a fully automatic washing machine is used to control the washing cycle without any human intervention. The cycle starts with the filling of water, after which the clothes are soaked and washed; thereafter the water is drained and the clothes are spin dry. The simple use of microcontroller has permitted repetitive execution of tedious tasks automatically without any human intervention, thereby saving precious time.
Data and Information
A computer is primarily for processing data. A computer system considers everything as data, be it instructions, pictures, songs, videos, documents, etc. Data can also be raw and unorganised facts that are processed to get meaningful information. So understanding the concept of data along with its different types is crucial to understand the overall functioning of a computer. Sometimes people use the terms data, information and knowledge interchangeably, which is incorrect.
Data and Its Types
A computer system has many input devices, which provide it with raw data in the form of facts, concepts, instructions, etc., Internally everything is stored in binary form (0 and 1), but externally, data can be input to a computer in the text form consisting of English alphabets A–Z, a–z, numerals 0–9, and special symbols like @, #, etc. Data can be input in other languages too or it can be read from the files. The input data may be from different sources, hence it may be in different formats. For example, an image is a collection of Red, Green, Blue (RGB) pixels, a video is made up of frames, and a fee receipt is made of numeric and non-numeric characters. Primarily, there are three types of data.
Structured Data
Data which follows a strict record structure and is easy to comprehend is called structured data. Such data with pre-specified tabular format may be stored in a data file to access in the future. Table 2 shows structured data related to monthly attendance of students maintained by the school.
| Student ID | Student Name | January | February | March | April | May | June | July | August | September | October | November | December |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 001 | John Doe | Present | Present | Absent | Present | Present | Present | Present | Present | Present | Present | Present | Present |
| 002 | Jane Smith | Present | Absent | Present | Present | Present | Present | Present | Present | Present | Absent | Present | Present |
| 003 | Michael Johnson | Present | Present | Present | Present | Present | Absent | Present | Present | Present | Present | Present | Present |
| 004 | Emily Brown | Present | Present | Present | Present | Absent | Present | Present | Present | Present | Present | Present | Absent |
| 005 | David Wilson | Absent | Present | Present | Present | Present | Present | Present | Present | Present | Present | Present | Present |
It is clear that such data is organised in row/column format and is easily understandable. Structured data may be sorted in ascending or descending order. In the example, attendance data is sorted in increasing order on the column ‘month’. Other examples of structured data include sales transactions, online railway ticket bookings, ATM transactions, etc.
Unstructured Data
Data which are not organised in a pre-defined record format is called unstructured data. Examples include audio and video files, graphics, text documents, social media posts, satellite images, etc. Figure 4 shows a report card with monthly attendance record details sent to parents. Such data are unstructured as they consist of textual contents as well as graphics, which do not follow a specific format.
Semi-structured Data
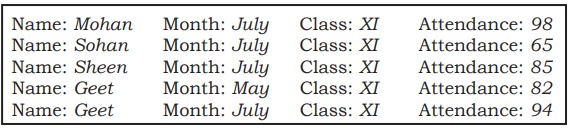
Data which have no well-defined structure but maintains internal tags or markings to separate data elements are called semi-structured data. Examples include email document, HTML page, comma separated values (csv file), etc. Figure 5 shows an example of semi-structured data containing student’s month-wise attendance details. In this example, there is no specific format for each attendance record. Here, each data value is preceded by a tag (Name, Month, Class, Attendance) for the interpretation of the data value while processing.
Data Capturing, Storage and Retrieval
To process data, we need to first input or capture the data. This is followed by its storage in a file or a database so that it can be used in the future. Whenever data is to be processed, it is first retrieved from the file or database so that we can perform further actions on it.
Data Capturing
It involves the process of gathering data from different sources in the digital form. This capturing may vary from simple instruments like keyboard, barcode readers used at shopping outlets , comments or posts over social media, remote sensors on an earth orbiting satellite, etc. Sometimes, heterogeneity among data sources makes data capturing a complex task.
Data Storage
It is the process of storing the captured data for processing later. Now-a-days data is being produced at a very high rate, and therefore data storage has become a challenging task. However, the decrease in the cost of digital storage devices has helped in simplifying this task. There are numerous digital storage devices available in the market like as shown in Figure 1.7.
Data keeps on increasing with time. Hence, the storage devices also require to be upgraded periodically. In large organisations, computers with larger and faster storage called data servers are deployed to store vast amount of data. Such dedicated computers help in processing data efficiently. However, the cost (both hardware and software) of setting up a data server as well as its maintenance is high, especially for small organisations and startups.
Data Retrieval
It involves fetching data from the storage devices, for its processing as per the user requirement. As databases grow, the challenges involved in search and retrieval of the data in acceptable time, also increase. Minimising data access time is crucial for faster data processing.
Data Deletion and Recovery
Data deletion and recovery are crucial aspects of data management and cybersecurity. When data is deleted, it’s not completely erased from storage devices but marked as available space. Recovery methods aim to retrieve lost or deleted data, posing challenges and considerations for data privacy, security, and legal compliance.
Data Deletion Mechanisms:
- Normal Deletion: Deleting files through the operating system marks them as available space but doesn’t erase the actual data. The space is overwritten as new data is stored.
- Secure Deletion: Secure deletion tools overwrite deleted data multiple times to prevent recovery using forensic techniques. Examples include programs like Eraser, DBAN (Darik’s Boot and Nuke), and Secure Erase.
- File Shredding: File shredding utilities overwrite files with random data several times, making recovery nearly impossible. This method ensures sensitive data destruction.
Data Recovery Techniques:
- File System Recovery: Software tools like Recuva, TestDisk, and PhotoRec recover deleted files by scanning the file system for remnants of deleted data.
- Data Carving: Advanced recovery methods use data carving to reconstruct files from fragmented or partially overwritten data clusters.
- Forensic Recovery: Specialized forensic tools and techniques are used for legal investigations, extracting deleted data from storage devices.
Challenges and Considerations:
- Data Overwriting: Overwritten data decreases recovery chances, especially with secure deletion methods.
- Physical Damage: Data recovery from physically damaged storage devices requires specialized techniques and cleanroom environments.
- Privacy Concerns: Recovered data may include sensitive information, raising privacy and confidentiality concerns.
Legal and Compliance Aspects:
- Data Retention Policies: Organizations must adhere to data retention policies to determine data deletion timelines and practices.
- GDPR and CCPA: Data privacy regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) mandate secure data deletion practices to protect user privacy.
- Audit Trails: Maintaining audit trails of data deletion and recovery activities ensures transparency and compliance with legal requirements.
Best Practices:
- Regular Backups: Implementing regular data backups reduces the impact of data loss and facilitates recovery.
- Secure Deletion Tools: Use secure deletion tools for sensitive data to prevent unauthorized access or recovery.
- Data Recovery Plans: Develop and test data recovery plans to quickly recover critical data in case of accidental deletion or data loss incidents.
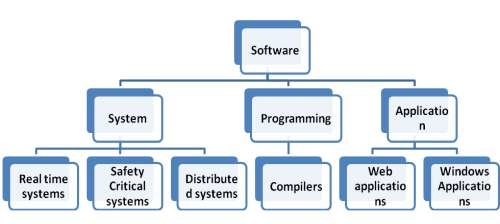
System Software
System software serves as the backbone of a computer system, providing essential functionalities to ensure its proper operation and efficient utilization of resources. It consists of several key components, including the operating system (OS), system utilities, and device drivers, each playing a vital role in managing hardware, software, and user interactions.
1. Operating System (OS):
- The operating system (OS) acts as a bridge between hardware and software, facilitating communication and resource allocation.
- Key functions of an OS include process management, memory management, file system management, device management, and user interface.
- Examples of popular operating systems include Microsoft Windows, macOS, Linux distributions (such as Ubuntu, Fedora, and Debian), Android, iOS, and Unix variants like FreeBSD and Solaris.
- Modern operating systems feature graphical user interfaces (GUIs), multitasking capabilities, virtual memory management, and security features like user authentication, access control, and encryption.
2. System Utilities:
- System utilities are software tools bundled with the operating system to perform various system management tasks and enhance user experience.
- Common system utilities include disk management tools (such as disk cleanup, disk defragmentation), backup and restore utilities, task managers, system monitoring tools, and performance optimization utilities.
- These utilities help users manage storage, monitor system resources, troubleshoot issues, and optimize system performance for efficient operation.
3. Device Drivers:
- Device drivers are software components that facilitate communication between the operating system and hardware devices such as printers, graphics cards, network adapters, and storage devices.
- Drivers act as intermediaries, translating OS commands into instructions that hardware devices understand and vice versa.
- Manufacturers provide device drivers specific to each hardware component, ensuring compatibility and proper functioning of hardware devices with the OS.
- Device drivers play a crucial role in plug-and-play functionality, allowing users to connect new devices to the system seamlessly.
Key Points on System Software:
- Integration: System software components work cohesively to ensure the smooth functioning of computing systems. The OS manages resources, system utilities aid in system maintenance and optimization, and device drivers enable hardware interaction.
- Updates and Maintenance: Regular updates and maintenance of system software are essential to address security vulnerabilities, implement bug fixes, enhance performance, and ensure compatibility with new hardware and software.
- Compatibility: System software must be compatible with hardware components and user applications to facilitate seamless operation and optimal performance of computing systems.
- User Interaction: System utilities provide users with tools to manage system resources, monitor system performance, troubleshoot issues, and customize system settings according to their preferences.
- Security: System software includes security features such as firewalls, antivirus software, encryption tools, and secure boot mechanisms to safeguard systems from threats, unauthorized access, and data breaches.
Application Software
The system software provides the core functionality of the computer system. However, different users need the computer system for different purposes depending upon their requirements. Hence, a new category of software is needed to cater to different requirements of the endusers. This specific software that works on top of the system software is termed as application software. There are again two broad categories of application software— general purpose and customised application software.
General Purpose Software
The application software developed for generic applications, to cater to a bigger audience in general are called general purpose software. Such ready-made application software can be used by end users as per their requirements. For example, spreadsheet tool Calc of LibreOffice can be used by any computer user to do calculation or to create account sheet. Adobe Photoshop, GIMP, Mozilla web browser, iTunes, etc., fall in the category of general purpose software.
Customized Software
These are custom or tailor-made application software, that are developed to meet the requirements of a specific organisation or an individual. They are better suited to the needs of an individual or an organisation, considering that they are designed as per special requirements. Some examples of user-defined software include websites, school management software, accounting software, etc. It is similar to buying a piece of cloth and getting a tailor-made garment with the fitting, colour, and fabric of our choice.
Proprietary or Free and Open Source Software
The developers of some application software provide their source code as well as the software freely to the public, with an aim to develop and improve further with each other’s help. Such software is known as Free and Open Source Software (FOSS). For example, the source code of operating system Ubuntu is freely accessible for anyone with the required knowledge to improve or add new functionality. More examples of FOSS include Python, Libreoffice, Openoffice, Mozilla Firefox, etc. Sometimes, software are freely available for use but source code may not be available. Such software are called freeware. Examples of freeware are Skype, Adobe Reader, etc. When the software to be used has to be purchased from the vendor who has the copyright of the software, then it is a proprietary software. Examples of proprietary software include Microsoft Windows, Tally, Quickheal, etc. A software can be freeware or open source or proprietary software depending upon the terms and conditions of the person or group who has developed and released that software.
Operating System
The operating system (OS) is a crucial software component that acts as an intermediary between users, applications, and computer hardware. It manages system resources and provides a platform for executing programs and performing tasks. An OS plays a fundamental role in enabling user interactions, managing memory, handling input/output operations, and ensuring overall system stability and security.
Functions of an Operating System:
- Process Management:
- Manages processes (programs in execution) by allocating resources, scheduling tasks, and facilitating communication between processes.
- Implements multitasking to allow concurrent execution of multiple processes, improving system efficiency and responsiveness.
- Memory Management:
- Allocates and deallocates memory space for programs and data, ensuring efficient utilization of available memory resources.
- Implements virtual memory techniques to allow processes to use more memory than physically available, reducing the risk of memory shortage.
- File System Management:
- Organizes and manages files and directories on storage devices (hard drives, SSDs) to enable data storage, retrieval, and organization.
- Provides file access controls, permissions, and security mechanisms to protect data integrity and prevent unauthorized access.
- Device Management:
- Controls and coordinates communication between hardware devices (printers, disk drives, network adapters) and the OS.
- Manages device drivers, which are software components that facilitate device communication and functionality.
- User Interface:
- Provides a user-friendly interface for interacting with the computer system, including graphical user interfaces (GUIs) and command-line interfaces (CLIs).
- Enables users to launch applications, manage files, configure system settings, and perform various tasks efficiently.
Types of Operating Systems:
- Single-User Operating Systems:
- Designed for individual users on personal computers and workstations.
- Examples include Microsoft Windows (Home editions), macOS, and some Linux distributions (Ubuntu Desktop).
- Multi-User Operating Systems:
- Support concurrent access and operation by multiple users on networked systems.
- Examples include Microsoft Windows Server, Linux distributions (such as CentOS, Debian), and UNIX variants.
- Real-Time Operating Systems (RTOS):
- Designed for applications that require real-time response and strict timing constraints.
- Used in embedded systems, industrial control systems, robotics, and aerospace applications.
- Examples include VxWorks, QNX, and FreeRTOS.
Importance of Operating Systems:
- Resource Management: OS efficiently manages system resources (CPU, memory, disk space) to optimize performance and ensure fair resource allocation among processes.
- Hardware Abstraction: Provides a layer of abstraction that allows applications to interact with hardware devices without needing to understand underlying hardware complexities.
- Security: Implements security measures such as user authentication, access control, encryption, and firewall protection to safeguard system integrity and data confidentiality.
- Application Support: Facilitates the execution of software applications by providing necessary services, libraries, and APIs (Application Programming Interfaces).
- User Experience: Enhances user experience through intuitive interfaces, seamless multitasking, and reliable system performance.
OS User Interface
The operating system (OS) user interface (UI) serves as the bridge between users and computer systems, providing a means for users to interact with applications, manage files, configure settings, and perform various tasks efficiently. The UI design plays a crucial role in enhancing user experience, productivity, and ease of use in computing environments.
Types of OS User Interfaces:
- Graphical User Interface (GUI):
- GUIs use graphical elements such as icons, windows, menus, buttons, and mouse pointers to facilitate user interactions.
- Examples include Microsoft Windows, macOS (Apple), GNOME (Linux), and Android/iOS mobile interfaces.
- Real-Life Example: Microsoft Windows 10 features a GUI with a Start menu, taskbar, and resizable windows for intuitive navigation and application management.
- Command-Line Interface (CLI):
- CLIs require users to enter text-based commands to perform operations and interact with the system.
- Common CLIs include Command Prompt (Windows), Terminal (macOS/Linux), PowerShell (Windows), and Bash (Linux).
- Real-Life Example: Command-line tools like Git use CLI for version control operations, code management, and collaboration among developers.
- Touch-Based User Interface (TUI):
- TUIs utilize touch-sensitive screens for user interactions, common in smartphones, tablets, and touch-enabled laptops.
- Examples include iOS and Android mobile interfaces, Windows 10 touchscreen mode, and touchscreen kiosks.
- Real-Life Example: The iOS interface on Apple iPhones and iPads allows users to navigate, access apps, and perform gestures (tap, swipe, pinch) for various functions.
Features and Components of OS User Interfaces:
- Desktop Environment (GUI):
- Provides a graphical desktop with icons, wallpaper, taskbar/dock, and system tray for launching applications and accessing system features.
- Real-Life Example: GNOME desktop environment in Linux distributions offers a customizable interface with a menu system, workspaces, and app launchers.
- Window Management (GUI):
- Manages multiple application windows, allowing users to arrange, resize, minimize, maximize, and switch between open windows.
- Real-Life Example: Windows OS supports window snapping, task view, and virtual desktops for efficient multitasking and organization of open windows.
- File Management (GUI and CLI):
- GUI file managers provide visual interfaces for browsing, organizing, copying, moving, renaming, and deleting files/folders.
- CLI file commands (e.g., ls, cd, mv, cp) allow users to manage files and directories using text-based commands in terminal/console.
- Real-Life Example: File Explorer (Windows), Finder (macOS), Nautilus (Linux GUI), and command-line file operations in Terminal (macOS/Linux) or Command Prompt (Windows).
- Application Launchers (GUI and CLI):
- GUIs feature application launchers (Start menu, dock, app drawer) for quickly accessing installed applications.
- CLIs use command syntax or aliases to launch applications and execute tasks directly from the terminal/command line.
- Real-Life Example: Start menu (Windows), Applications menu (Linux), Spotlight (macOS) for GUI; typing ‘firefox’ to launch Firefox browser in CLI.
Importance of OS User Interface:
- Accessibility: UI design considerations ensure accessibility features for users with disabilities (e.g., screen readers, high contrast modes, keyboard shortcuts).
- Productivity: Intuitive UI elements and workflows enhance user productivity by reducing learning curves, streamlining tasks, and providing quick access to essential functions.
- Customization: Many OSs allow UI customization (themes, layouts, shortcuts) to suit individual preferences and workflow requirements.
- Compatibility: UI consistency across devices and platforms improves user experience and compatibility with diverse hardware configurations.
- Feedback and Notifications: UI elements like notifications, alerts, and status indicators provide timely feedback and information to users about system events, updates, and notifications.
Functions of Operating System
An operating system (OS) is a fundamental software component that manages computer hardware and provides essential services to users, applications, and system processes. The functions of an operating system are diverse and crucial for the efficient operation of computer systems. Here is a comprehensive overview of the key functions performed by an operating system:
1. Process Management:
- Process Creation: The OS creates and manages processes, which are instances of executing programs. It allocates resources such as CPU time, memory, and I/O devices to processes.
- Process Scheduling: The OS employs scheduling algorithms to prioritize and schedule processes for execution on the CPU. It ensures fair resource allocation and optimal system performance.
- Process Termination: When a process completes its execution or encounters an error, the OS terminates the process, releases allocated resources, and performs cleanup tasks.
2. Memory Management:
- Memory Allocation: The OS manages physical memory (RAM) by allocating memory space to processes as needed. It tracks memory usage, assigns memory addresses, and handles memory requests from applications.
- Virtual Memory: OS implements virtual memory techniques, allowing processes to use more memory than physically available. It uses disk space as an extension of RAM, swapping data between RAM and disk when needed.
- Memory Protection: OS enforces memory protection mechanisms to prevent unauthorized access or modification of memory areas. It ensures data integrity and system security.
3. File System Management:
- File Creation and Deletion: The OS facilitates the creation, deletion, and manipulation of files and directories. It manages file metadata, permissions, and access control.
- File Access: OS provides file access methods and APIs for applications to read, write, and modify files. It ensures efficient file storage, retrieval, and organization.
- File System Integrity: The OS maintains file system integrity by implementing file system consistency checks, error handling mechanisms, and backup/restore functionalities.
4. Device Management:
- Device Allocation: The OS manages I/O devices such as printers, disk drives, network adapters, and USB devices. It allocates device resources, handles device requests, and manages device drivers.
- Device Drivers: OS includes device drivers, which are software modules that facilitate communication between the OS and hardware devices. Drivers enable device functionality and support plug-and-play operations.
- Interrupt Handling: OS handles device interrupts, which are signals generated by hardware devices to request attention or report events. It manages interrupt priorities, dispatches interrupt service routines, and ensures timely device responses.
5. User Interface:
- Graphical User Interface (GUI): OS provides a graphical user interface (GUI) for users to interact with the system. GUI elements include windows, icons, menus, buttons, and desktop environments. It enhances user experience and facilitates application navigation.
- Command-Line Interface (CLI): OS supports command-line interfaces (CLIs) for advanced users and system administrators. CLIs allow users to enter text commands to execute tasks, manage files, configure settings, and troubleshoot issues.
Additional Functions:
- Security Management: OS implements security features such as user authentication, access control, encryption, firewalls, and antivirus protection to safeguard system resources and data.
- Networking: OS supports networking functionalities for communication between computers, devices, and network services. It manages network protocols, connections, and data transmission.
- System Monitoring: OS includes monitoring tools and utilities to track system performance, resource utilization, errors, and events. It provides insights into system health and helps diagnose issues.
- Backup and Recovery: OS facilitates data backup, recovery, and restoration processes. It ensures data integrity, fault tolerance, and disaster recovery capabilities.
Operating systems play a critical role in providing an interface between hardware and software components, managing system resources, ensuring system stability, and enabling users to interact with computing devices effectively. The functions performed by an OS are essential for the reliable, secure, and efficient operation of modern computer systems.
Name the software required to make a computer functional. Write down its two primary services.
The software required to make a computer functional is an Operating System (OS). Its two primary services are:
- Process Management: The OS manages processes, which are instances of executing programs. It allocates resources such as CPU time, memory, and I/O devices to processes, schedules their execution, and handles process termination and cleanup.
- Memory Management: The OS manages computer memory by allocating and deallocating memory space for programs and data. It tracks memory usage, assigns memory addresses, implements virtual memory techniques, and enforces memory protection mechanisms to ensure efficient and secure memory utilization.
How does the computer understand a program written in high level language?
A computer understands a program written in a high-level language through a process called compilation or interpretation. Here’s how it works:
- Compilation: When a program is written in a high-level language like C, C++, Java, or Python, it needs to be converted into machine code (binary code) that the computer’s CPU can directly execute. This conversion process is performed by a compiler. The steps involved in compilation are as follows:
- The programmer writes the program using high-level language syntax and constructs.
- The program is then fed into a compiler, which analyzes the code, checks for syntax errors, and translates it into an intermediate form known as object code or assembly code.
- The object code is further processed by the linker, which combines it with necessary libraries and system files to generate an executable file (binary file) containing machine code instructions.
- The computer’s CPU can directly execute the machine code instructions, allowing the program to run and perform its intended tasks.
- Interpretation: In contrast to compilation, interpretation involves directly executing high-level code without prior conversion into machine code. An interpreter reads and executes the program line by line, translating each statement into machine instructions on-the-fly. This process occurs during runtime, without generating an intermediate executable file. Languages like Python, JavaScript, and Ruby are typically interpreted languages.
- The programmer writes the program in a high-level language.
- The interpreter reads the code line by line, analyzes each statement, and executes the corresponding machine instructions immediately.
- This approach allows for faster development and easier debugging, as changes made to the code can be tested immediately without the need for recompilation.
